13 Best Free Digital Forensic Tools For Windows
Here is a list of Best Free Digital Forensic Tools For Windows. In this article, you will find a variety of digital forensic tools. With the help of these forensic tools, forensic inspectors can find what had happened on a computer.
While some forensic tools let you capture the RAM of the system, some can capture the browser’s history. All the browsers’ history including bookmarks, cached files, cookies, downloads, form history, saved logins, searches, etc. will be captured by these software. Besides this, you will also get screenshots of the web pages you visit.
You will also find some software which have the power to capture the hashes (MD5, SHA1, SHA256, etc.) of multiple files. I have also listed a software in this list which comes with OS Fingerprinting feature.
A software in this run-down lists all the activities of the user. For example, software installation, opening a file/folder, login or logout information, etc.
Some software let you save the analyzed data in different formats, like TXT, HTML, CSV, etc.
If the user encrypts the data of a computer, there is also a software to detect such type of activity. It scans the hard drives and detects the encrypted data (if any). Explore the article to know about the supported encryption volumes.
FAW (Forensic Aquisition of Websites) is a new revolution in the world of digital forensics. It is the first forensic web browser, widely used by the forensic experts to minimise the cyber crimes. Read the article to know more about it.
My Favorite Digital Forensic Tools:
Autopsy is my favorite digital forensic tool for Windows. It comes with many important features, like Web Artifact Analysis, Timeline Analysis, Multi-User Cases, Registry Analysis, etc.
I also like Network Miner. You can extract the data transferred over a network by using this free digital forensic tool. It is the only software in this list, which comes with OS Fingerprinting feature.
You may also like some best free VPN Software, Hurricane Tracking Software, and Lead Management Software for Windows.
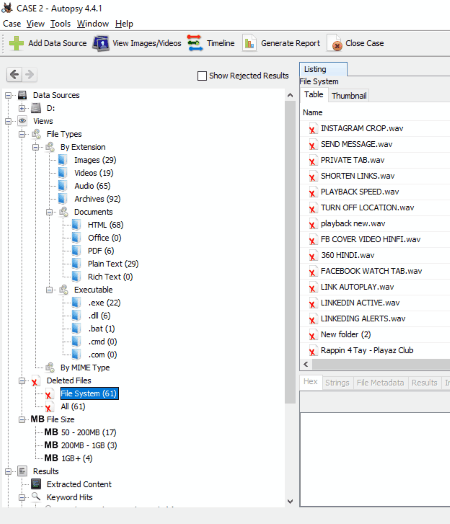
Autopsy
Autopsy is an open source forensic tool for Windows. It is one of the most popular forensic software which are used by the forensic experts to investigate all unauthorized access. Also, it offers a lot of features which make it an important tool in the field of digital forensics.
Have a look at its features:
- Autopsy allows you to create multi-user cases. So, you can view the results of your team members in real time. This feature helps examiners to solve complex/large cases quickly.
- Timeline Analysis helps examiners analyze all the activities occurred on the entire system. The software generates a bar graph with respect to time which shows how frequently an activity has taken place on the system.
- Web Artifact Analysis: This feature actually captures the users’ information from some of the popular web browsers (Firefox, Chrome, Internet Explorer, etc.). This information includes bookmarks, history, cookies, downloads, etc.
- Registry Analysis: A digital forensic examiner can extract all the data from Windows registry.
- By Link File Analysis, officers can examine shortcuts and documents accessed by a user.
- EXIF: Using this feature, the forensic experts can extract the geographical location and camera information from JPEG files.
- If the user has done any change in a software, forensic experts can detect this by matching the digital signatures.
- Autopsy also has a feature to extract the user data from an Android Smartphone, such as SMS, Call Log, Contacts, etc.
- If you are looking for a particular file, you can find that by using Keyword Search feature. For Email Addresses, Phone Numbers, IP Addresses, and URLs, Autopsy follows the regular expression search pattern by default.
Besides the above-listed features, Autopsy offers some more useful features.
All in all, Autopsy is a complete software in the field of digital forensics which is available free of cost.
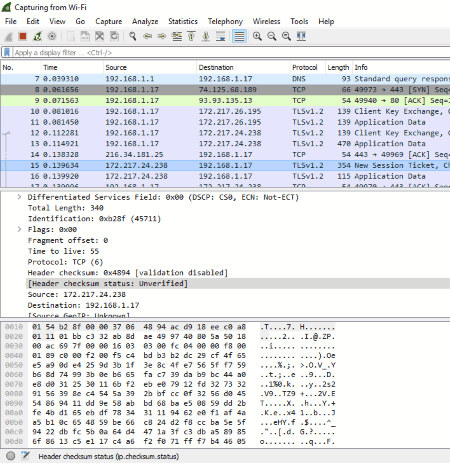
Wireshark
Wireshark is one of the most widely used network capture and analysis tool for Windows. Hence, it can be used in a forensic investigation. You can view all the activities going on in a network.
Once you launch the Wireshark, it starts capturing the network information in the form of packets. These packets display the following information: Time, Source IP Address, Destination IP Address, Protocol (TCP, ARP, etc.), Length, and Info. The Info part provides further information about the network being captured by Wireshark, like Application Data, Encryption Alert, Standard Query, etc.
This free digital forensic tool also provides a search feature. You can use this feature to search a particular packet within the list of packets being captured by the software. Moreover, you can also apply filters to your searches. Three types of filters are available in the software: Hex Value, String, and Regular Expression. Besides this, you can also make case-sensitive searches.
It has a live capturing feature, hence it keeps you updated with network packets. You can also enable the feature to automatically scroll to the bottom during live capture to view latest updates. Besides this, it also lets you analyze the captured data offline.
Apart from the above listed features, it also allows you read/write multiple captured file formats, like tcpdump (libpcap), Pcap NG, Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer (compressed and uncompressed), Sniffer Pro, and NetXray, Network Instruments Observer, NetScreen snoop, etc.
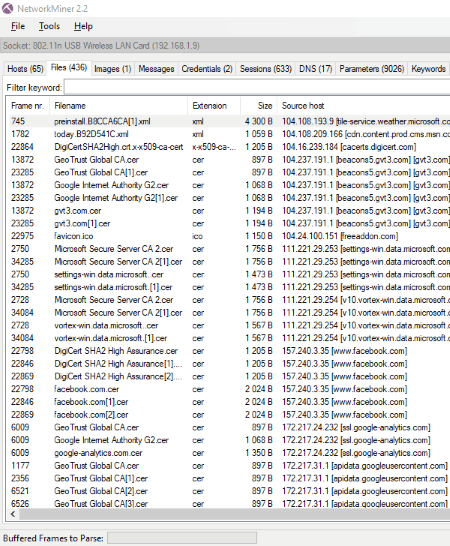
NetworkMiner
NetworkMiner is another free digital forensic software. It is actually a network analyzer forensic tool, which is designed to capture IP Address, MAC Address, Host Name, Sent Packets, Received Packets, Sent Bytes, Received Bytes, No. of Open TCP Ports, Operating System, etc. The good part of the software is that it captures all the data without putting any traffic on the network.
It also comes with a feature to extract files, emails, certificates, etc. transferred over a network. All this information can be parsed in PCAP Files, so that the forensic experts could analyze the generated reports offline. The PCAP parsing speed in the free version of the software is 2.31MB/s. You can use this feature to extract and save the files streamed over the network by the user. Following are the supported formats to extract the files from the internet: FTP, TFTP, HTTP, SMB, SMB2, SMTP, POP3, and IMAP.
Apart from the above-listed features, the free version of this software has a very important feature, named OS Fingerprinting. OS Fingerprinting is a technique used by forensic experts to detect the Operating Systems used by a person/host.
This free digital forensic tool also captures the screenshots and save them as thumbnails. Such an information can be viewed in the Images tab of the software.
NetworkMiner is also capable to capture the important information of the user, like his username and passwords. But this feature is limited to some supported protocols. Such an information is displayed in the Credential tab of the software. You can copy the username and password and paste it at any location on your PC. The software copied the username well but failed to copy the user password during testing. Moreover, it also has a feature to calculate MD5, SHA1, and SHA256 hashes of captured files.
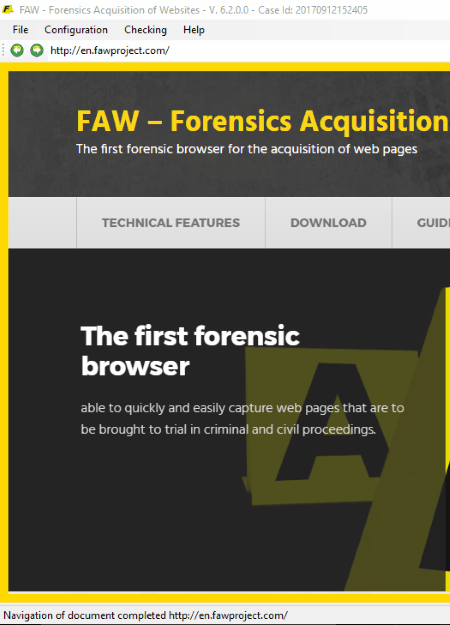
FAW (Forensic Acquisition of Websites)
FAW (Forensic Acquisition of Websites) is a first forensic web browser in the field of digital forensics. It provides a feature of web page acquisition for forensic investigation. The interface of this free forensic tool is similar to a web browser, which comprises of an address bar, forward button, a backward button, a Go To an Address button, a reload button, and a stop search button. You can search any webpage by typing its address in the address bar.
You can navigate any website with this forensic web browser for a partial or total acquisition of web pages. While acquiring a web page, it also captures all the images on that webpage and saves them at a default location. Moreover, it also has a feature to record all the ongoing activities on the screen during the acquisition process.
It also has an advanced feature to acquire the web pages that contain streaming videos, i.e., videos running on Javascript, Flash, etc.
Apart from this, it also acquires the entire HTML code of web pages being launched in the software. During the web page acquisition, it generates separate files in TXT format, which contain frames and headers of the web page.
This free digital forensic tool also offers Social Media Acquisition. Using FAW, you can access any social media network in order to acquire it. Besides this, it also calculates MD5 and SHA1 hashes automatically.
You can save all the analyzed data on the FAW’s remote server. It also captures all the traffic from all the active networks of a web page, hence, helps investigators to analyze the network traffic.
FAW also has advanced configuration options. It displays the same web page differently to different user agents. For this, an HTTP prefix “User-agent” or “User-Agent” is used.
The good part of this free forensic tool is that it generates a summary report for each acquisition, which contains a detailed log of all the operations performed by a forensic expert and files created by him along with the time.
All in all, FAW (Forensic Acquisition of Websites) is a great tool in the field of digital forensics, which comes with many advanced features to acquire different websites.
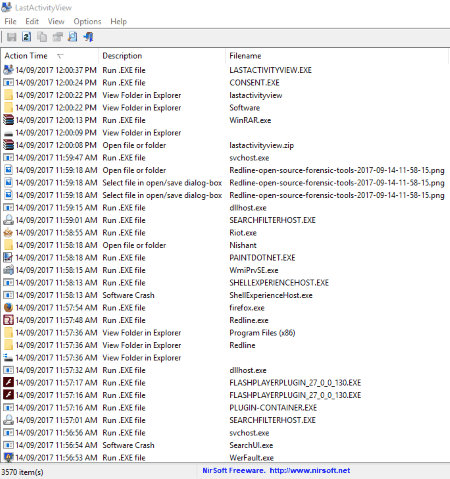
LastActivityView
LastActivityView is another free digital forensic tool for Windows. It lets forensic experts view all the user activities on a computer. For example, the changes done by the user on a computer, files viewed by him, etc. In Advanced Options, you can view the users’ activity for past “X” days, hours, minutes, and seconds.
You will get a detailed information about all the actions taken by the user, which include action time and date, description, file name, complete file path, etc. The description part of the software displays the summary of all actions taken by the user for a particular file or folder, for example, opening a file or folder, selected file in open/save dialog box, running an EXE file, running a software installation, system shutdown or reboot information, blue screen error, system crash information, system sleep information, user login and logoff information, and more. Besides this, if the user viewed any file in the Windows Explorer, it also displays this information. Double click on any of the displayed items to view the same information in a tabular format.
It has a search option, which you can use to search a particular file in the database. You can modify the searches as Match Case and Match Whole Word Only. You can save all or selected items in TXT, CSV, HTML, and XML formats.
This free digital forensic tool reads all the archives files by default. You can change this setting in Options menu.
To eliminate complexity in viewing the items, you can enable Mark Odd/Even feature, which highlights odd and even rows with white and gray colors respectively.
It also generates HTML reports for all or selected items and launches this report on your default web browser. This feature of the software sounds good, but it didn’t work while testing.
You can directly open the main directory of any of the selected item(s). For this, click File > Open Folder in Explorer or simply press F2 key.
Image Forensic Search System
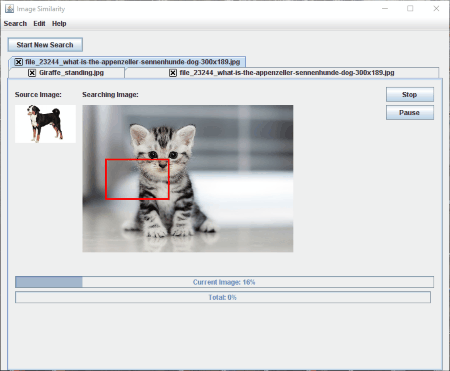
Image Forensic Search System is a very useful digital forensic tool, which can be used to search specific images. It is an open source forensic software, which forensic experts can use to search the target image of a victim or guilty person in the computer’s directory or in an image set.
It features three types of image search options:
- Search a target image within another image: Using this feature, you can search the target image hidden in an image set, like Panorama, Collage, etc. This feature didn’t work for me; not sure if I missed something during testing.
- Search for similar images within a selected directory: This feature lets forensic experts search the target image within a selected directory. The software will then compare all the images similar to the target image and displays the result.
- Search for source image within every image in the selected directory: If you enable this feature, the software will search the source image among all the images stored in the selected directory.
Human Mode is an interesting feature of this software, enabling which the software also looks at skin areas and colors in the images while comparing the human faces.
You can do more than one image search at a time. All your searches will be carried in different tabs.
Browser History Capturer
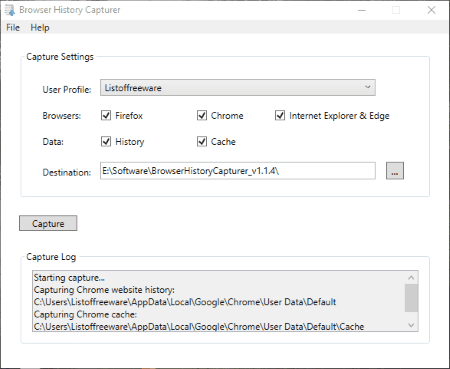
Browser History Capturer is a free digital forensic tool. It is a portable software and is designed to capture a web browser history from a computer. Following are the web browsers supported by this software: Mozilla Firefox (version 3 or higher), Google Chrome (all versions), Internet Explorer (version 10 or higher), and Microsoft Edge (all versions).
Just launch the software and click on Capture button and it starts capturing the history of above-listed web browsers, no matter whether the web browsers are running in the background or not. It saves all the captured data at a default location on your PC, which can be changed by the user. The captured data includes bookmarks, cached files, cookies, downloads, form history, saved logins, searches, website history, etc. It also captures the screenshots of the web pages visited by the user. You will find all the screenshots in thumbnails folder.
Magnet RAM Capture
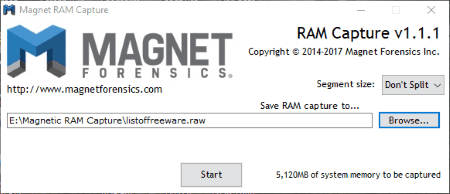
Magnet RAM Capture is another free digital forensic tool. It is a portable software and is designed to help investigators to analyze the data found only in the system’s memory. The captured information includes currently running programs, network connection information, usernames and passwords, decrypted files and keys, etc.
The captured data is saved in Raw format. Keep sure that you have enough space on disk, as the data requires large space to be stored. The file stored on my computer after RAM capturing was of 5 GB.
This free digital forensic tool also has an option to split the forensic file among 500MB, 1GB, 2GB, and 4GB.
All in all, Magnet RAM Capture is a powerful digital forensic tool, which is intended to capture all the evidence that is not stored on the local hard drive.
Belkasoft Live RAM Capturer
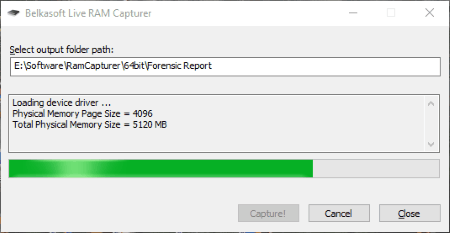
Belkasoft Live RAM Capturer is a free and powerful digital forensic tool. It has the power to capture all the data in the computer’s RAM, no matter whether the data is protected or not. Since it can capture all the protected and unprotected data on the computer’s volatile memory, it is one of the best free forensic tools for forensic experts for memory capture.
To capture the forensic evidence on RAM, simply launch the software > select the output path to store the captured data > click on Capture button. As simple as that.
NOTE: The captured file requires large space on disk.
HashMyFiles
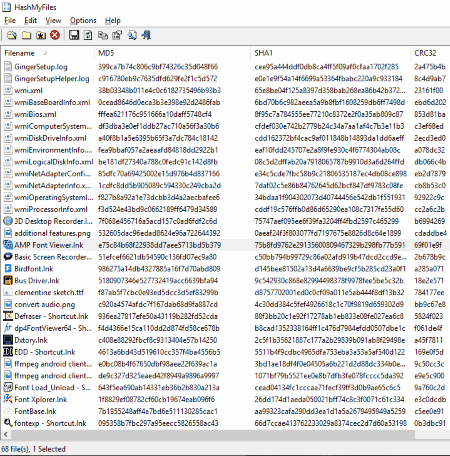
HashMyFiles is a simple yet effective digital forensic tool for Windows. It is developed to calculate MD5, SHA1, CRC32, SHA256, SHA512, and SHA384 hashes of multiple files on your computer. Simply open the files and it will calculate the hashes automatically. You can easily copy the MD5, SHA1, CRC32, and SHA256 hashes either by right clicking or by using the function keys defined for them. Along with the hashes, it also displays some other information of all opened files, such as File Path, File Extension, File Attribute, Modified Time, File Size, etc. Moreover, it also has an option to be launched directly from Windows context menu.
You can save the data as Text File, Tab Delimited Text File, Tabular Text File, HTML File, XML File, and CSV File.
Open in VirusTotal Website feature of this software lets you scan any file directly at VirusTotal portal. A single click will open the selected file on VirusTotal portal for scanning.
Passware Encryption Analyzer
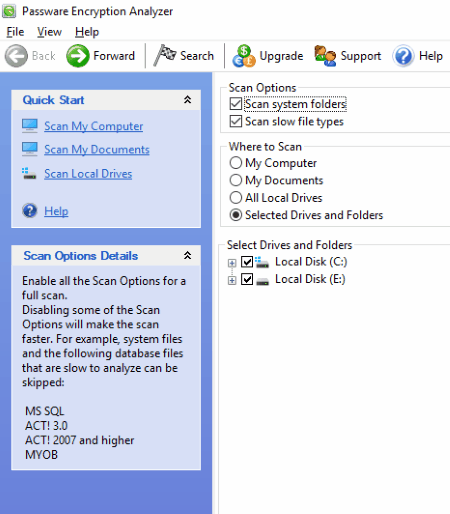
Passware Encryption Analyzer is another free digital forensic tool for Windows. It scans the entire system or selected hard drives and detects the protected and encrypted data.
It comes with a fast scanning speed. I scanned disk containing 50GB data and it took about 10 minutes to scan it. While scanning the system, it also displays the scanning speed in two different formats. The scanning speed that it displayed during scanning 50GB data was more than 5000 files/minute and approx 400MB/minute. Do note that the scanning speed does not remain constant.
After the completion of a scan, it displays all the protected items found along with protection methods and encryption types. If any encrypted file is detected by the software, it also displays the password recovery options and decryption complexity for that.
NOTE: The free version of this software only lets you analyse the files for forensic research. You cannot save the result in this free version.
RedLine
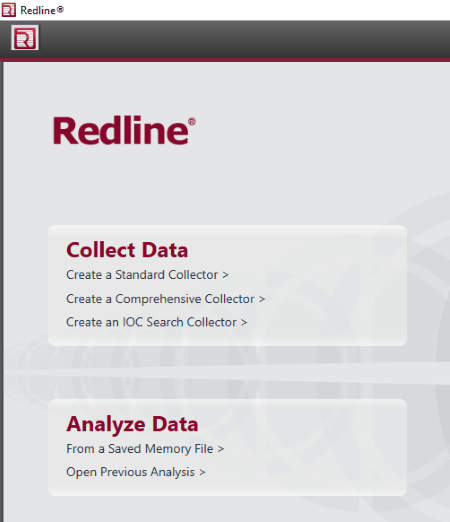
RedLine is another powerful digital forensic tool in this list. It offers two features: Collect Data and Analyze Data. Forensic officers can use Analyze Data feature to analyze files and memory on a computer. File and memory analyzing techniques help forensic examiners to find the forensic evidence on a computer.
Collect Data collects all the information from the computer, like running processes and drivers from memory, file-system metadata, registry data, event logs, network information, services, tasks, etc.
NOTE: Make sure that you should have a memory dump file on your computer before making any attempt to Analyze Data. If you don’t have a memory dump file, you have to first perform the Collect Data process.
Encrypt Disk Detector
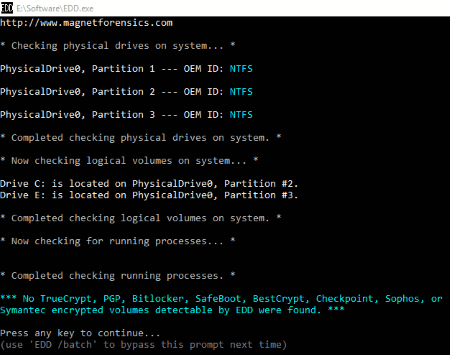
Encrypt Disk Detector is another free digital forensic tool for Windows. It is a command prompt based application that scans all the disks on your computer and detects the encrypted data (if any). This will help the forensic investigators to check what actually has happened to the system. So that, they could take an appropriate action.
Encrypt Disk Detector scans the hard drives of the computer for the following volumes: TrueCrypt, BitLocker, SafeBoot, Semantic Encrypted Volumes, etc.
About Us
We are the team behind some of the most popular tech blogs, like: I LoveFree Software and Windows 8 Freeware.
More About UsArchives
- May 2024
- April 2024
- March 2024
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- July 2019
- June 2019
- May 2019
- April 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- April 2017
- March 2017
- February 2017
- January 2017
- December 2016
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- April 2016
- March 2016
- February 2016
- January 2016
- December 2015
- November 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014